- +1-315-215-1633
- sales@thebrainyinsights.com

Global security and vulnerability management market is expected to reach USD 15.86 billion by 2030, at a CAGR of 9% from 2021 to 2030. Defending against a continuous information security breach is a challenge for businesses of all sizes. Security professionals are projected to remain ahead of the threats by using technology, policies, and procedures to secure sensitive data and prevent incoming attacks, resulting in market growth.
In terms of information technology, data security refers to the safeguarding of various forms of information including confidential data. Various technology, training, and techniques are employed for this purpose. A vulnerability is any way through which an external threat actor can gain unauthorised access or privileged control over an application, service, endpoint, or server. Communication ports that are open to the internet, insecure software or operating systems, techniques for gaining privileged access through approved interaction with a specific application or operating system, and a vulnerability to malware infection are all tangible examples. A security vulnerability is an unexpected feature of a computing component or system configuration that increases the probability of an undesirable occurrence or a loss owing to accidental disclosure, deliberate attack, or conflict with new system components. Exploited vulnerabilities could cause IT systems to fail, resulting in costly data breaches and service disruptions. Vulnerability management refers to the methods, techniques, and tactics used to detect, evaluate, treat, and report security vulnerabilities and misconfigurations in software and systems inside a company. In other words, it enables one to continuously monitor the company's digital environment for potential threats, providing them with an up-to-date view of the present security situation. It is a proactive technique to identify, manage, and mitigate network vulnerabilities so that enterprise applications, software, and devices are more secure.
Get an overview of this study by requesting a free sample
Increased instances of cyber-threats and cyber-attacks will emerge as key market growth drivers. The market's growth will be accelerated by the rapid increase in data volume and the growing demand for efficient and effective data security systems. Increased digital transformation initiatives, increased usage of connected devices, and a surge in the proliferation of the internet and smartphones are all contributing to the market's growth.
Internal vulnerabilities, such as insider trading, will limit the market's expansion. The market's growth rate will be further slowed by a lack of proper risk-prioritizing parameters. The market's growth will be slowed by the high deployment costs associated with the systems.
Mobile device vulnerability assessment, cloud computing, and software vulnerability assessment have all grown in line with the IT and telecommunications industries. The rising use of cloud computing has increased the possibility of vulnerability attacks on cloud networks. The public cloud, private cloud, and hybrid cloud technologies are accessed to the servers of many organisations because cloud managed services are best suited for use in various IT firms due to their cost effectiveness and high speed internet. As a result of these advantages, cloud computing use is on the rise, propelling the market forward.
Despite the numerous benefits of security and vulnerability management, small and medium businesses frequently encounter resource constraints that prevent them from implementing security and vulnerability management systems. Furthermore, many businesses suffer funding issues. These reasons are impeding the market's expansion.
The global security and vulnerability management market has been segmented based on size of organization and end-user industry and regions.
The regions analyzed for the market include North America, Europe, South America, Asia Pacific, and the Middle East and Africa. North America region emerged as the largest market for the global security and vulnerability management market with a 34.8%share of the market revenue in 2020.
North America region Security and Vulnerability Management Market Share in 2020 - 36.9%
www.thebrainyinsights.com
Check the geographical analysis of this market by requesting a free sample
The key players are now concentrating on implementing strategies such as adopting new technology, product innovations, mergers & acquisitions, joint venture, alliances, and partnerships to improve their market position in the global security and vulnerability management industry.
In Nov 2019, Qualys, Inc. announced its new Vulnerability Management, Detection, and Response (VMDR) app, which streamlines the scanning, investigation, prioritisation, and neutralisation of threats for customers. VMDR is a single tool that includes Asset Discovery and Inventory, Vulnerability Assessment with Configuration Controls, Prioritization, Remediation, and Audit.
On 5th of March, 2019 Tripwire, Inc. announced the extension of its Tripwire Expert Ops service. Vulnerability management was added as a managed service as part of this expansion. This Expert Ops can handle vulnerability security management, which is especially useful for firms with limited in-house cyber security management.
As per The Brainy Insights, the size of the security and vulnerability management market was valued at USD 6.7 Billion in 2020 to USD 15.86 Billion by 2030.
Global security and vulnerability management market is growing at a CAGR of 9% during the forecast period 2021-2030.
The global security and vulnerability management market has been segmented based on size of organization, end-user industry, and regions. The large enterprises segment led the extruder segment in 2020.
North America region emerged as the largest market for the security and vulnerability management.
The market's growth will be influenced by rising cases of cyber threats and cyber-attacks.
Breach of security could hamper the market growth.
Cloud computing, mobile device and software development, and vulnerability assessment are all on the rise which will provide huge opportunities to the market.
Key players areAlien Vault, Broadcom Inc., Dell EMC, EMC Corporation, Hewlett-Packard, IBM Corporation, Microsoft Corporation, Netiq Corporation, Qualys, Rapid 7, Skybox Security and Tripwire.
1. Introduction
1.1. Objectives of the Study
1.2. Market Definition
1.3. Research Scope
1.4. Currency
1.5. Key Target Audience
2. Research Methodology and Assumptions
3. Executive Summary
4. Premium Insights
4.1. Porter’s Five Forces Analysis
4.2. Value Chain Analysis
4.3. Top Investment Pockets
4.3.1. Market Attractiveness Analysis BySize of Organization
4.3.2. Market Attractiveness Analysis ByEnd-user Industry
4.3.3. Market Attractiveness Analysis By Region
4.4. Industry Trends
5. Market Dynamics
5.1. Market Evaluation
5.2. Drivers
5.2.1. Rising cases of cyber threats and cyber-attacks
5.3. Restraints
5.3.1. Breach of security
5.4. Opportunities
5.4.1. Cloud computing, mobile device and software development, and vulnerability assessment are all on the rise
5.5. Challenges
5.5.1. Lack of funds and resources
6. Global Security and Vulnerability Management Market Analysis and Forecast, By Size of Organization
6.1. Segment Overview
6.2. Large Enterprises
6.3. Small and Medium Enterprises
7. Global Security and Vulnerability Management MarketAnalysis and Forecast, By End-user Industry
7.1. Segment Overview
7.2. Aerospace
7.3. Retail
7.4. Manufacturing
7.5. Defense and Intelligence
7.6. BFSI
7.7. Healthcare
7.8. IT and Telecommunication
8. Global Security and Vulnerability Management Market Analysis and Forecast, By Regional Analysis
8.1. Segment Overview
8.2. North America
8.2.1. U.S.
8.2.2. Canada
8.2.3. Mexico
8.3. Europe
8.3.1. Germany
8.3.2. France
8.3.3. U.K.
8.3.4. Italy
8.3.5. Spain
8.4. Asia-Pacific
8.4.1. Japan
8.4.2. China
8.4.3. India
8.5. South America
8.5.1. Brazil
8.6. Middle East and Africa
8.6.1. UAE
8.6.2. South Africa
9. Global Security and Vulnerability Management Market-Competitive Landscape
9.1. Overview
9.2. Market Share of Key Players in GlobalSecurity and Vulnerability Management Market
9.2.1. Global Company Market Share
9.2.2. North America Company Market Share
9.2.3. Europe Company Market Share
9.2.4. APAC Company Market Share
9.3. Competitive Situations and Trends
9.3.1. Product Launches and Developments
9.3.2. Partnerships, Collaborations, and Agreements
9.3.3. Mergers & Acquisitions
9.3.4. Expansions
10. Company Profiles
10.1. Alien Vault
10.1.1. Business Overview
10.1.2. Company Snapshot
10.1.3. Company Market Share Analysis
10.1.4. Company Product Portfolio
10.1.5. Recent Developments
10.1.6. SWOT Analysis
10.2. Broadcom Inc.
10.2.1. Business Overview
10.2.2. Company Snapshot
10.2.3. Company Market Share Analysis
10.2.4. Company Product Portfolio
10.2.5. Recent Developments
10.2.6. SWOT Analysis
10.3. Dell EMC
10.3.1. Business Overview
10.3.2. Company Snapshot
10.3.3. Company Market Share Analysis
10.3.4. Company Product Portfolio
10.3.5. Recent Developments
10.3.6. SWOT Analysis
10.4. EMC Corporation
10.4.1. Business Overview
10.4.2. Company Snapshot
10.4.3. Company Market Share Analysis
10.4.4. Company Product Portfolio
10.4.5. Recent Developments
10.4.6. SWOT Analysis
10.5. Hewlett-Packard
10.5.1. Business Overview
10.5.2. Company Snapshot
10.5.3. Company Market Share Analysis
10.5.4. Company Product Portfolio
10.5.5. Recent Developments
10.5.6. SWOT Analysis
10.6. IBM Corporation
10.6.1. Business Overview
10.6.2. Company Snapshot
10.6.3. Company Market Share Analysis
10.6.4. Company Product Portfolio
10.6.5. Recent Developments
10.6.6. SWOT Analysis
10.7. Microsoft Corporation
10.7.1. Business Overview
10.7.2. Company Snapshot
10.7.3. Company Market Share Analysis
10.7.4. Company Product Portfolio
10.7.5. Recent Developments
10.7.6. SWOT Analysis
10.8. Netiq Corporation
10.8.1. Business Overview
10.8.2. Company Snapshot
10.8.3. Company Market Share Analysis
10.8.4. Company Product Portfolio
10.8.5. Recent Developments
10.8.6. SWOT Analysis
10.9. Qualys
10.9.1. Business Overview
10.9.2. Company Snapshot
10.9.3. Company Market Share Analysis
10.9.4. Company Product Portfolio
10.9.5. Recent Developments
10.9.6. SWOT Analysis
10.10. Rapid 7
10.10.1. Business Overview
10.10.2. Company Snapshot
10.10.3. Company Market Share Analysis
10.10.4. Company Product Portfolio
10.10.5. Recent Developments
10.10.6. SWOT Analysis
10.11. Skybox Security
10.11.1. Business Overview
10.11.2. Company Snapshot
10.11.3. Company Market Share Analysis
10.11.4. Company Product Portfolio
10.11.5. Recent Developments
10.11.6. SWOT Analysis
10.12. Tripwire
10.12.1. Business Overview
10.12.2. Company Snapshot
10.12.3. Company Market Share Analysis
10.12.4. Company Product Portfolio
10.12.5. Recent Developments
10.12.6. SWOT Analysis
List of Table
1. Global Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
2. Global Large Enterprises Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
3. Global Small and Medium Enterprises Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
4. Global Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
5. Global Aerospace Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
6. Global Retail Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
7. Global ManufacturingSecurity and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
8. Global Defense and Intelligence Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
9. Global BFSI Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
10. Global Healthcare Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
11. Global IT and Telecommunication Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
12. Global Security and Vulnerability Management Market, By Region, 2018–2030 (USD Billion)
13. Global Security and Vulnerability Management Market, By North America, 2018–2030 (USD Billion)
14. North America Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
15. North America Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
16. U.S. Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
17. U.S. Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
18. Canada Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
19. Canada Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
20. Mexico Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
21. Mexico Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
22. Europe Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
23. Europe Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
24. Germany Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
25. Germany Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
26. France Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
27. France Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
28. U.K. Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
29. U.K. Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
30. Italy Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
31. Italy Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
32. Spain Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
33. Spain Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
34. Asia Pacific Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
35. Asia Pacific Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
36. Japan Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
37. Japan Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
38. China Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
39. China Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
40. India Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
41. India Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
42. South America Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
43. South America Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
44. Brazil Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
45. Brazil Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
46. Middle East and Africa Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
47. Middle East and Africa Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
48. UAE Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
49. UAE Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
50. South Africa Security and Vulnerability Management Market, By Size of Organization, 2018–2030 (USD Billion)
51. South Africa Security and Vulnerability Management Market, By End-user Industry, 2018–2030 (USD Billion)
List of Figures
1. Global Security and Vulnerability Management Market Segmentation
2. Security and Vulnerability Management Market: Research Methodology
3. Market Size Estimation Methodology: Bottom-Up Approach
4. Market Size Estimation Methodology: Top-Down Approach
5. Data Triangulation
6. Porter’s Five Forces Analysis
7. Value Chain Analysis
8. Global Security and Vulnerability Management Market Attractiveness Analysis BySize of Organization
9. Global Security and Vulnerability Management Market Attractiveness Analysis ByEnd-user Industry
10. Global Security and Vulnerability Management Market Attractiveness Analysis By Region
11. Global Security and Vulnerability Management Market: Dynamics
12. Global Security and Vulnerability Management Market Share BySize of Organization (2021&2030)
13. Global Security and Vulnerability Management Market Share ByEnd-user Industry(2021&2030)
14. Global Security and Vulnerability Management Market Share by Regions (2021&2030)
15. Global Security and Vulnerability Management Market Share by Company (2020)
This study forecasts revenue at global, regional, and country levels from 2018 to 2030. The Brainy Insights has segmented the global security and vulnerability management market based on below mentioned segments:
Global Security and Vulnerability Management Market by Size of Organization:
Global Security and Vulnerability Management Market byEnd-user Industry:
Global Security and Vulnerability Management Market by Region:
Research has its special purpose to undertake marketing efficiently. In this competitive scenario, businesses need information across all industry verticals; the information about customer wants, market demand, competition, industry trends, distribution channels etc. This information needs to be updated regularly because businesses operate in a dynamic environment. Our organization, The Brainy Insights incorporates scientific and systematic research procedures in order to get proper market insights and industry analysis for overall business success. The analysis consists of studying the market from a miniscule level wherein we implement statistical tools which helps us in examining the data with accuracy and precision.
Our research reports feature both; quantitative and qualitative aspects for any market. Qualitative information for any market research process are fundamental because they reveal the customer needs and wants, usage and consumption for any product/service related to a specific industry. This in turn aids the marketers/investors in knowing certain perceptions of the customers. Qualitative research can enlighten about the different product concepts and designs along with unique service offering that in turn, helps define marketing problems and generate opportunities. On the other hand, quantitative research engages with the data collection process through interviews, e-mail interactions, surveys and pilot studies. Quantitative aspects for the market research are useful to validate the hypotheses generated during qualitative research method, explore empirical patterns in the data with the help of statistical tools, and finally make the market estimations.
The Brainy Insights offers comprehensive research and analysis, based on a wide assortment of factual insights gained through interviews with CXOs and global experts and secondary data from reliable sources. Our analysts and industry specialist assume vital roles in building up statistical tools and analysis models, which are used to analyse the data and arrive at accurate insights with exceedingly informative research discoveries. The data provided by our organization have proven precious to a diverse range of companies, facilitating them to address issues such as determining which products/services are the most appealing, whether or not customers use the product in the manner anticipated, the purchasing intentions of the market and many others.
Our research methodology encompasses an idyllic combination of primary and secondary initiatives. Key phases involved in this process are listed below:
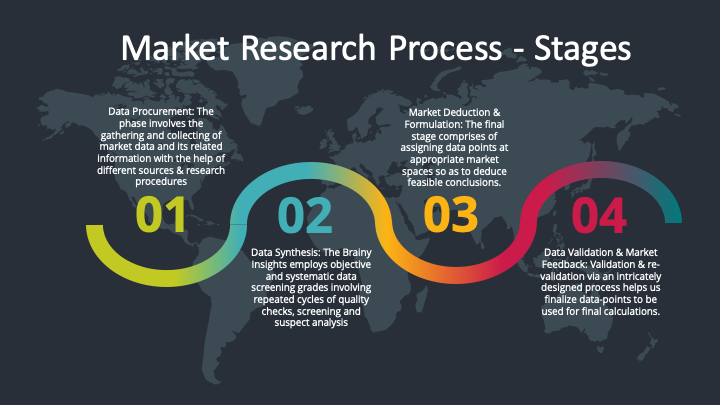
The phase involves the gathering and collecting of market data and its related information with the help of different sources & research procedures.
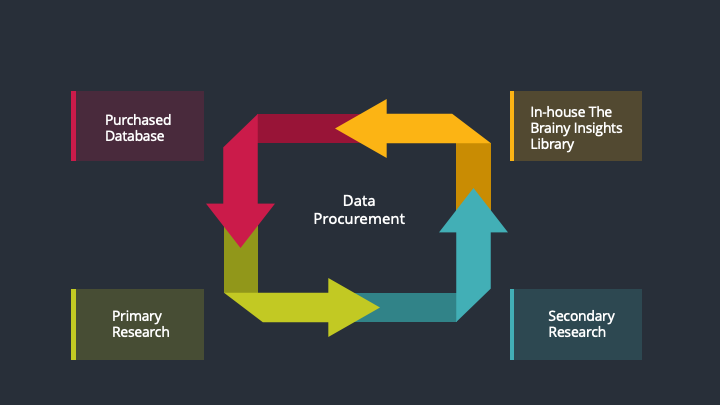
The data procurement stage involves in data gathering and collecting through various data sources.
This stage involves in extensive research. These data sources includes:
Purchased Database: Purchased databases play a crucial role in estimating the market sizes irrespective of the domain. Our purchased database includes:
Primary Research: The Brainy Insights interacts with leading companies and experts of the concerned domain to develop the analyst team’s market understanding and expertise. It improves and substantiates every single data presented in the market reports. Primary research mainly involves in telephonic interviews, E-mail interactions and face-to-face interviews with the raw material providers, manufacturers/producers, distributors, & independent consultants. The interviews that we conduct provides valuable data on market size and industry growth trends prevailing in the market. Our organization also conducts surveys with the various industry experts in order to gain overall insights of the industry/market. For instance, in healthcare industry we conduct surveys with the pharmacists, doctors, surgeons and nurses in order to gain insights and key information of a medical product/device/equipment which the customers are going to usage. Surveys are conducted in the form of questionnaire designed by our own analyst team. Surveys plays an important role in primary research because surveys helps us to identify the key target audiences of the market. Additionally, surveys helps to identify the key target audience engaged with the market. Our survey team conducts the survey by targeting the key audience, thus gaining insights from them. Based on the perspectives of the customers, this information is utilized to formulate market strategies. Moreover, market surveys helps us to understand the current competitive situation of the industry. To be precise, our survey process typically involve with the 360 analysis of the market. This analytical process begins by identifying the prospective customers for a product or service related to the market/industry to obtain data on how a product/service could fit into customers’ lives.

Secondary Research: The secondary data sources includes information published by the on-profit organizations such as World bank, WHO, company fillings, investor presentations, annual reports, national government documents, statistical databases, blogs, articles, white papers and others. From the annual report, we analyse a company’s revenue to understand the key segment and market share of that organization in a particular region. We analyse the company websites and adopt the product mapping technique which is important for deriving the segment revenue. In the product mapping method, we select and categorize the products offered by the companies catering to domain specific market, deduce the product revenue for each of the companies so as to get overall estimation of the market size. We also source data and analyses trends based on information received from supply side and demand side intermediaries in the value chain. The supply side denotes the data gathered from supplier, distributor, wholesaler and the demand side illustrates the data gathered from the end customers for respective market domain.
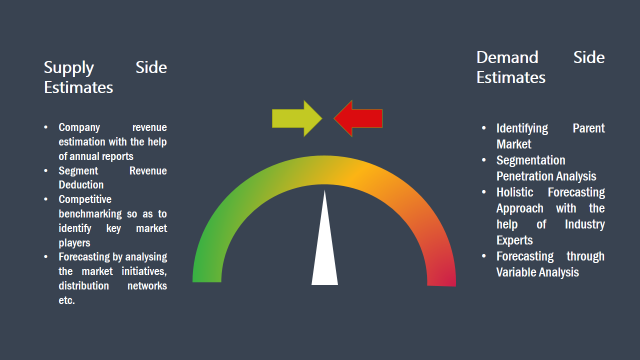
The supply side for a domain specific market is analysed by:
The demand side for the market is estimated through:
In-house Library: Apart from these third-party sources, we have our in-house library of qualitative and quantitative information. Our in-house database includes market data for various industry and domains. These data are updated on regular basis as per the changing market scenario. Our library includes, historic databases, internal audit reports and archives.
Sometimes there are instances where there is no metadata or raw data available for any domain specific market. For those cases, we use our expertise to forecast and estimate the market size in order to generate comprehensive data sets. Our analyst team adopt a robust research technique in order to produce the estimates:
Data Synthesis: This stage involves the analysis & mapping of all the information obtained from the previous step. It also involves in scrutinizing the data for any discrepancy observed while data gathering related to the market. The data is collected with consideration to the heterogeneity of sources. Robust scientific techniques are in place for synthesizing disparate data sets and provide the essential contextual information that can orient market strategies. The Brainy Insights has extensive experience in data synthesis where the data passes through various stages:
Market Deduction & Formulation: The final stage comprises of assigning data points at appropriate market spaces so as to deduce feasible conclusions. Analyst perspective & subject matter expert based holistic form of market sizing coupled with industry analysis also plays a crucial role in this stage.
This stage involves in finalization of the market size and numbers that we have collected from data integration step. With data interpolation, it is made sure that there is no gap in the market data. Successful trend analysis is done by our analysts using extrapolation techniques, which provide the best possible forecasts for the market.
Data Validation & Market Feedback: Validation is the most important step in the process. Validation & re-validation via an intricately designed process helps us finalize data-points to be used for final calculations.
The Brainy Insights interacts with leading companies and experts of the concerned domain to develop the analyst team’s market understanding and expertise. It improves and substantiates every single data presented in the market reports. The data validation interview and discussion panels are typically composed of the most experienced industry members. The participants include, however, are not limited to:
Moreover, we always validate our data and findings through primary respondents from all the major regions we are working on.
Free Customization
Fortune 500 Clients
Free Yearly Update On Purchase Of Multi/Corporate License
Companies Served Till Date